|
Closed
|
Case #
|
10044
|
|
Affiliated Job:
|
New Trier Township District 2031
|

|
|
Opened:
|
Thursday, October 14, 2010
|
|
Closed:
|
Thursday, October 14, 2010
|
|
Total Hit Count:
|
21417
|
|
Last Hit:
|
Tuesday, April 16, 2024 4:29:50 AM
|
|
Unique Hit Count:
|
5861
|
|
Last Unique Hit:
|
Tuesday, April 16, 2024 4:29:50 AM
|
|
Case Type(s):
|
Development, Server
|
|
|
Case Notes(s):
|
All cases are posted for review purposes only. Any implementations should be performed at your own risk.
|
|
|
|
Project:
|
|
We are making use of Google Apps EDU to host our student email addresses and provide the Google Docs and other features Google Apps offers to our student body. Google is absolutely terrible for support of their products and uses APIs to interface with features such as SSO which requires a third party source to service this function. After some research the below is our solution to add SSO integration with our Active Directory environment.
|
|
|
Action(s) Performed:
|
|
Total Action(s): 1
|
|
Action #
|
Recorded Date
|
Type
|
Hit(s)
|
User
|
Expand Details
|
|
10154
|
10/14/2010 1:36:26 PM
|
Server
|
3427
|
contact@danieljchu.com
|
Some sample illustrations of the Single Sign On for Google Apps are shown b Collapse ...
|
Last Hit: Tuesday, April 16, 2024 3:10:44 AM
Some sample illustrations of the Single Sign On for Google Apps are shown below.
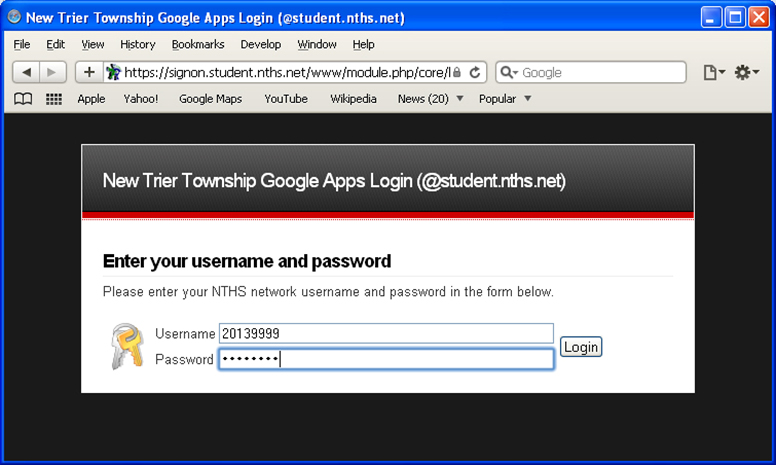
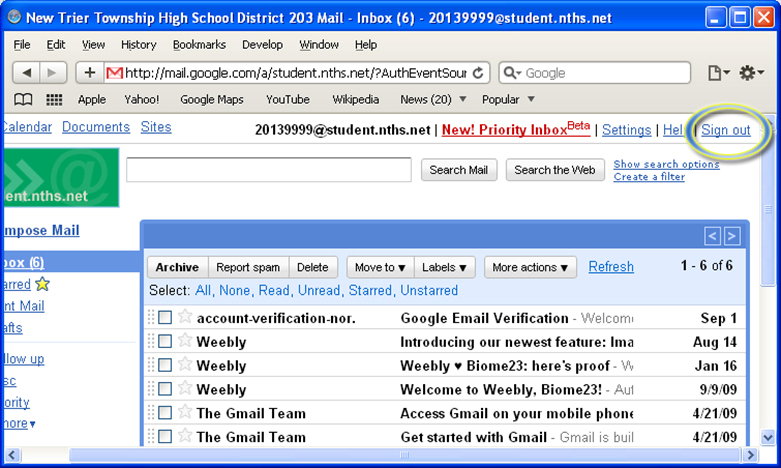
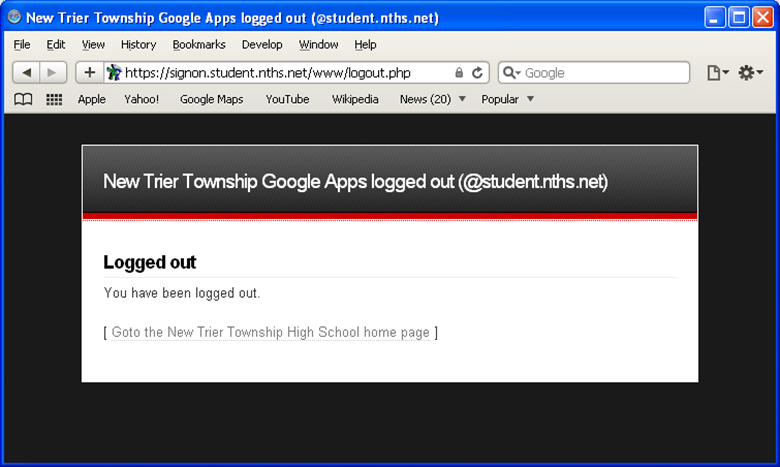
If you use a self signed SSL certificate, users may see these type of messages:
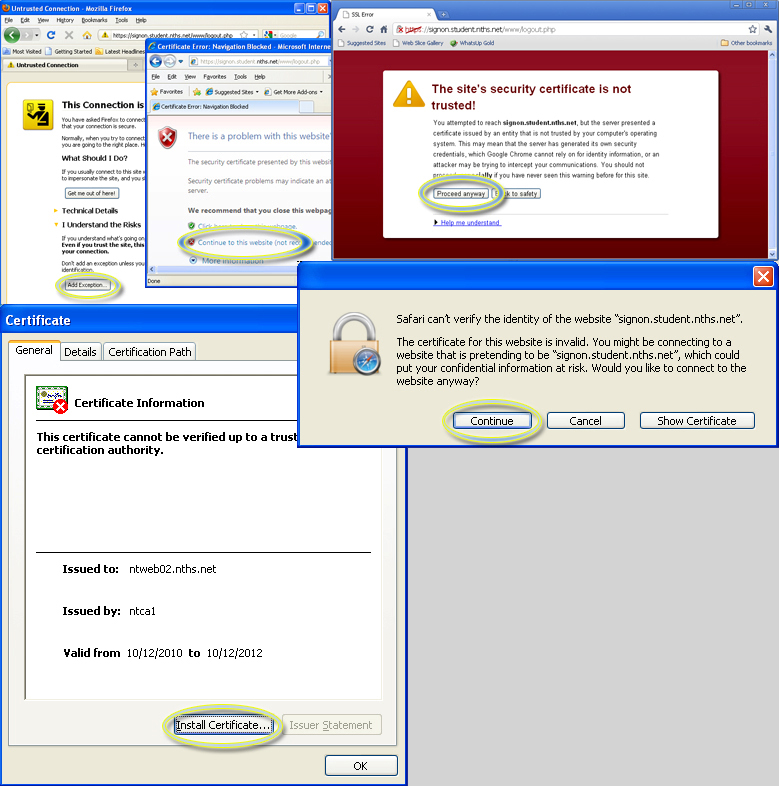
|
|
|
|
|
Outcome:
|
Google offers lists of supported third party options, from managing the Google Apps accounts to service SSO support with your authentication infrastructure. We decided to use the "simpleSAMLphp" option, PHP script which offers multiple types of web based authentication services.
Download this set of code onto a server supporting PHP server side script, in our case we are using a Windows 2003 server with PHP integrated into IIS. It took me a while to completely figure out the integration process, but overall it is fairly simplistic. The things you will need are as follows:
| - | PHP supported web server (outside facing) | | - | Download the SimpleSAMLphp script: http://simplesamlphp.org/download | | - | SSL (either through an internal CA or through a registrar such as Verisign or Entrust) |
My instructions will assume you are using a Windows based IIS server with an internal Windows based certificate authority. Note illustration included above, if you use an internal SSL expect any device that does not trust the root certificate authority will demonstrate the prompts demonstrated in the illustration. Therefore you may want to acquire a SSL through a vendor such as Verisign or Entrust.
| - | Uncompress the contents of the download into a new site container where you plan to host the SSO site | | | | o | You can place the containing folders at the root of a new site container (i.e. www/) | | o | Or, place these folders in an existing site under a sub folder (i.e. signon/www/) |
| | - | For me, I found a glitch in the code and copied the "www" off the root as a second directory duplicating the files into a new folder, also at the root, labeled "simplesaml" | | - | Create the custom SSL private & public keys through your Windows based Certificate Authority | | | | o | I am using a multi-site (subject name alternative) wild card web server certificate, I have instructions for creating a certificate through a Windows certificate authority, just goto: http://www.danieljchu.com/DanielJChu-CaseRedirect.asp?hdnCaseID=/CaseID/15-55.asp& | | o | Once you have your certificate, you need to break it out into two files, a "google.pem" (private key file) & a "google.crt" (certificate file) | | | | > | Once you have your certificate imported onto your server's personal store, export the certificate out including the private key into a pfx file | | > | Goto: https://www.sslshopper.com/ssl-converter.html & upload the pfx file, select to convert it to a "Standard PEM" file type - enter the password you selected when you exported out the pfx file | | > | The resulting pem file is a text based file which you can then copy/paste out the two sections into a single pem and crt file. | | | | 1. | Extract the section with "-----BEGIN RSA PRIVATE KEY-----" / "-----END RSA PRIVATE KEY-----" and place this into a new file which you will save as google.pem | | 2. | Extract the section with "-----BEGIN CERTIFICATE-----" / "-----END CERTIFICATE-----" and place this into a new file which you will save as google.crt |
| | > | Place these two resulting files into the "cert" folder | | > | The certificate used for communication with Google Apps (The above instructions) may be different then the certificate used to secure the website hosted on IIS |
|
| | - | Go into the "config" folder and edit the config.php file | | | | o | Modify the paths at the beginning to reflect where items are... such as the "baseurlpath" which is initially set to "simplesaml/", but I changed this to "www/" if you choose to host this in an existing site under a subdirectory such as "/signon" then this "baseurlpath" ONLY should have this included path in front (i.e. signon/www/). The rest are probably fine as they are... | | o | Proceed through the rest of the variables defining other items, such as "auth.adminpassword", "secretsalt", "technicalcontact_email" | | o | For Google Apps SSO, set the "enable.saml20-idp" => true, (Default is false) |
| | - | Also in the "config" folder, edit the authsources.php file | | | | o | I went through and REM'ed out the top authentication options (use "/*" to start a REM statement and "*/" to end a REM statement) | | o | For the A.D. integration, un-REM (remove the beginning "/*" and trailing "*/") for the "example-ldap" authentication section and modify the varable entries defining your LDAP information. | | | | > | Change the name of the section from "example-ldap" to something like "company-ldap" | | > | 'hostname' => 'server.domain.net', | | > | 'dnpattern' => 'cn=%username%,ou=users,dc=domain,dc=net', | | > | 'search.enable' => TRUE, | | > | 'search.base' => array('OU=User Container 01,DC=domain,DC=net', 'OU=User Container 02,DC=domain,DC=net'), | | > | 'search.attributes' => array('sAMAccountName', 'mail'), | | > | 'search.username' => 'CN=ldapuser,CN=Users,DC=domain,DC=net', | | > | 'search.password' => 'WhatEverThePasswordIs' |
|
| | - | Next, modify two files in the "metadata" folder | | | | o | saml20-idp-hosted.php | | | | > | 'privatekey' => 'google.pem', | | > | 'certificate' => 'google.crt', | | > | 'auth' => 'company-ldap', |
| | o | saml20-sp-remote.php | | | | > | REM out the "Example simpleSAMLphp" section | | > | 'AssertionConsumerService' => 'https://www.google.com/a/yourdomain.domain.net/acs', | | > | Add the line: 'spNameQualifier' => 'google.com', | | > | 'simplesaml.nameidattribute' => 'sAMAccountName', |
|
| | - | Customize the wording of the default layout by modifying the appropriate pages located in the "dictionaries" folder | | - | Customize the layouts by reviewing the code in the folders: | | | | o | "www" | | o | "templates" | | | | > | "header.php" and "footer.php" files in "templates/includes" |
| | o | "modules\core\www" | | o | "modules\core\templates" |
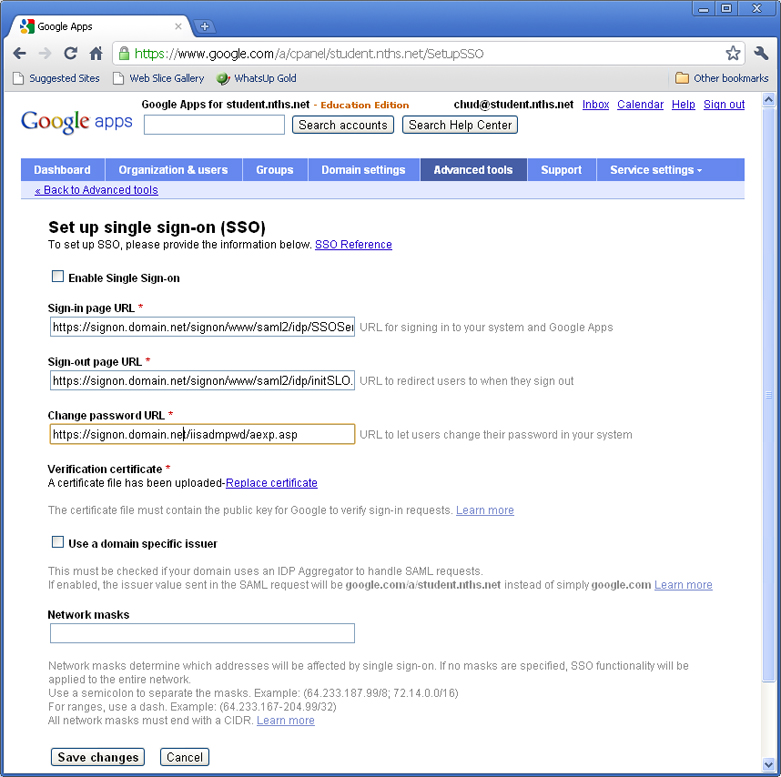
| | - | Update Google Apps to activate the SSO. To test it out, I logged into Google Apps using one type of browser, retaining my logged in state and switching on SSO, then using a different browser to test it out so I could easily turn SSO back off in my original browser window. Be aware your logged in state does eventually time out... | | - | A screen capture included above shows the settings | | | | o | Goto your Google Apps administration dashboard -> Advanced Tools -> "Setup single sign-on (SSO)" | | o | Sign-in page URL: | | | | > | https://signon.domain.net/signon/www/saml2/idp/SSOService.php |
| | o | Sign-out page URL: | | | | > | https://signon.domain.net/signon/www/saml2/idp/initSLO.php?RelayState=/www/logout.php | | | | 1. | ?RelayState=/www/logout.php (if at root of site) | | 2. | ?RelayState=/signon/www/logout.php (if in a sub folder of an existing site) |
|
| | o | Change password URL: |
|
| | | > | Can be bogus, just needs to be something, perhaps instructions/contact or the IISADMPWD on IIS 6.0 |
| | o | Upload your certificate google.crt file for "Verification certificate" | | o | Click "Save changes" | | o | When you are ready to test/enable, check the "Enable Single Sign-on" checkbox and click "Save changes" again. |
|
The process is when a user goes to log into Google Apps, Google will redirect them to the Sign-in URL which is hosted on your server, they enter the username/password affiliated with your LDAP integration which is then verified, the PHP script redirects the user back to Google using the "sAMAccountName" which should match the username in Google Apps and grants them access to the appropriate mailbox.
When the user logs out, they are redirected back to the PHP script to unauthenticated their presence. Some screen captures are included above for review...
|
|
|
|
|
|
|
|

